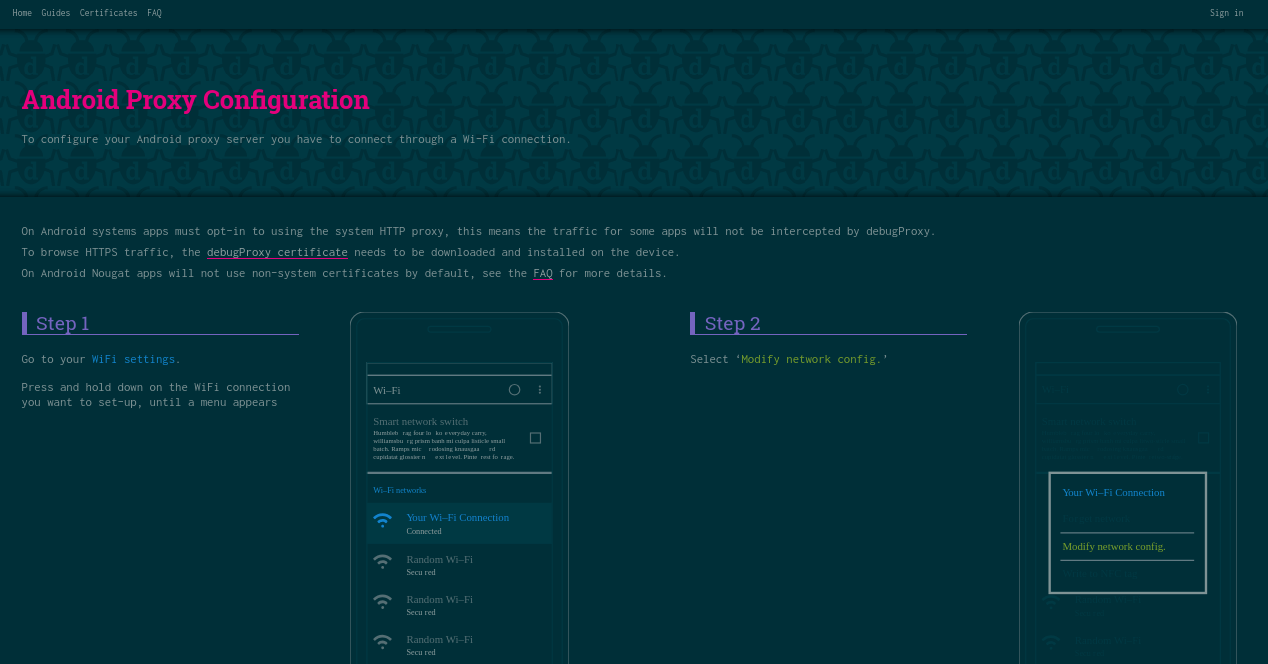
Download Wireshark Apk For Android
- Wifi Pass Breaking: Wifite - Aircrack - Wireshark For Android .
- Unable To Use Androiddump In Windows With . - Wireshark
- 38 Best FireStick Apps (Sep 2019) Free Movies, Shows, Live TV, Sports
- Want To Test My Android For Hacked Activity [closed] - Ask .
Dialectical behavior therapy skills workbook pdf download. In my review of the iHealth glucometer I pointed out that I did indeed check if the app talked with the remote service over TLS or not. This was important because if it didn’t, it meant it was sending medical information over plaintext. There are a few other things that can go wrong, they can for instance not validate the certificate provided over TLS, effectively allowing MITM attacks to succeed, but that’s a different story altogether, so I won’t go there for now.
Wireshark is a network packet analyzer. A network packet analyzer will try to capture network packets and tries to display that packet data as detailed as possible. You could think of a network packet analyzer as a measuring device used to examine what’s going on inside a network cable. As an additional platform wireshark is now available for Android operating system as well. The smartphones which run android can download the wireshark apk from the Google Play Store with a safe and easy manner. Features Of Wireshark Apk. There are some highlighted features in wireshark apk. Wireshark calls into extcap, that calls into androiddump, that calls into adb, that calls into tcpdump on the device. And here is the problem: my device (a Sony Xperia XA from 3 Ireland) has indeed a tcpdump command, but the only thing it does is returning 1 as return value, and that’s it. After that search for “Wireshark “and install the app on your chromebook. If your Chromebook is not compatible you can download the Play store apk and installing it manually, After that you can follow the steps mentioned above to find the “Wireshark ” app and install it on your device. Installing Wireshark using Chrome Browser.

What I wanted to write about is some notes about my experience, if nothing else because it took me a while to get all the fragments ready, and I could not find a single entry anywhere that would explain what the error message I was receiving was about.
First of all, this is about the Wireshark tool, and Android phones, but at the end of the day you’ll find something that would work almost universally with a bunch of caveats. So make sure you get your Wireshark installed, and make sure you never run it as root for your own safety.
Rick suggested to look into the androiddump tool that comes with Wireshark; on Gentoo that requires enabling the right USE flag. This uses the extcap interface to “fetch” the packets to display from a remote source. I like this idea among other things because it splits the displaying/parsing from the capturing. As I’ll show later, this is not the only useful tool using the interface.
There are multiple interfaces that androiddump can capture from; that does include the logcat output, that makes it very useful when you’re debugging an application in realtime, but what I cared about was sniffing the packets from the interfaces on the device itself. This kept failing with the following error:
Error by extcap pipe: ERROR: Broken socket connection.
And no further debugging information available. Googling for a good half hour didn’t bring me anywhere, I even started strace‘ing the process (to the point that Wireshark crashed in a few situations!) until I finally managed to figure out the right -incantation- invokation of the androiddump tool… that had no more information even in verbose mode, but at least it told me what it was trying to do.
The explanation is kind of simple: this set of interfaces is effetively just a matrioska of interfaces. Wireshark calls into extcap, that calls into androiddump, that calls into adb, that calls into tcpdump on the device.
And here is the problem: my device (a Sony Xperia XA from 3 Ireland) has indeed a tcpdump/download-spss-18-dengan-crack.html. command, but the only thing it does is returning 1 as return value, and that’s it. No error message and not even a help output to figure out if you need to enable somethihng. I have not dug into the phone much more because I was already kind of tired of having to figure out pieces of the puzzle that are not obvious at all, so I looked for alternative approaches.
Depending on the working system you use to set the capture up, you may be able to set up your computer to be an access point, and connect the phone to it. But this is not easy particularly on a laptop with already-oversubscribed USB ports. So I had to look for alternatives.
On the bright side, my router is currently running OpenWRT (with all the warts it has). Which means I have som leeway on the network access already. Googling around would suggest setting up a tee: tell iptables to forward a copy of every single packet coming from or to the phone to another mac address. This is relativel expensive, and no reliable over WiFi networks anyway, beside increasing congestion on an already busy network.
I opted instead to use another tool that is available in extcap: ssh-based packet captures. In Gentoo these require the sshdump and libssh USE flags enabled. With this interface, Wireshark effectively opens a session via SSH to the router, and runs tcpdump on it. It can also use dumpcap or tshark, which are Wireshark-specific tools, and would be significantly more performant, but there is no build for them on OpenWRT so that does not help either.
While this actually increases the amount of traffic over WiFi compared to the tee option, it does so over a reliable channel, and it allows you to apply capture filters, as well as start and stop capture as needed. I ended up going for this option, and the good thing with this is that if you know the hardware addresses of your devices, you can now very easily sniff any of the connected clients just by filtering on that particular address, which opens for interesting discoveries. But that’s for another day.
18 Jul 2016Wireshark (originally named Ethereal) is a free and open source packet analyzer.It is used for network troubleshooting, analysis, software and communications protocol development, and education. [1]It functions similar to pcap in terms of packet capturing, yet its major feature is the network protocol analysis which pcap cannot offer.According to the official site, “Wireshark is the world’s foremost network protocol analyzer.” [2] Though Wireshark has distribution on all major platforms: GNU/Linux, OS X, BSD, Solaris, some other Unix-like operating systems, and Microsoft Windows, there is no official distribution for Android or common embedded Linux platform.Some reader may know that for Android, there is an app called ``Shark for Root’’ on Google Play Store [3], but it is only an encapsulation of the tcpdump binary for Android.
I will discuss the major steps to cross-compile Wireshark libraries for the Android platform.This post is based on my experience compiling the Wireshark 2.0.x libraries for Android on Ubuntu 14.04/16.04.
To my best knowledge, this post is the first comprehensive guide on how to cross-compile the latest Wireshark for Android.But still, this is NOT an easy task, at all.You should anticipate to encounter new errors in your attempts, but be able to fix them with reasonable knowlege of compiling and programming.Only for tech-savvy people.(Don’t be intimidated, I am joking! Download rhino 5 full crack for mac. :P)
DISCLAIMER:Though I believe that this post should work on most of the Linux distributions and subsequent Wireshark 2.0.x releases, and should be easily extended to other embedded Linux platforms, I cannot guarantee that it will work.
Install required packages
In this post, I assume the building system is Ubuntu 16.04 64-bit.The following packages needs to be installed.
Compile and install dependency libraries
If you directly starting to compile Wireshark using the cross compiler, most probably you will be stopped here:
You can see, like many other open-source softwares, Wireshark depends on GLib.So you need to have GLib (>= 2.16.0) cross-compiled and installed in order to cross-compile Wireshark.The GLib cross-compilation process was discussed in detail in my previous blog (Cross-compile GLib for Android).Also make sure that GLib’s install location is included in the PATH, otherwise ld will complain that it cannot find -lglib-2.0.so and so on.
Download Wireshark sources
Download Wireshark sources from its official website.The latest stable version is 2.0.4.For example, the download link from North America CDN is: https://2.na.dl.wireshark.org/src/wireshark-2.0.4.tar.bz2.
Patch the Wireshark source codes
Because Android does not fully support some of the standard Unix functions, (such as endgrent()), we need to make several patches.
Wifi Pass Breaking: Wifite - Aircrack - Wireshark For Android .
You will then be prompted that some function signatures do not match.
The first one is that some function signatures do not match their implementations.We need to change the function signature of void *DtdParseAlloc() at line 64 in epan/dfilter/dfilter-int.h.Change the input type from void *(*)(gsize) to void* (*mallocProc)(size_t).Same patch is needed for another occurance of it in file epan/dtd_parse.h, line 25.
The second patch we need to apply is in tools/lemon/Makefile.in at line 775.The lemon is one of Wireshark’s essential internal building tool.We need to change $(CC_FOR_BUILD) to its absolute path /usr/bin/cc assuming we are using the standard GCC install location.This is actually a bug in lemon’s environment configuration.The $(CC_FOR_BUILD) is supposed to be interpreted as the build system’s CC which is /usr/bin/cc, but in fact it will be wrongly taken as the host system’s CC which is the arm-eabi version when we cross-compile.That would be an error because lemon has to be built as the executable for the build system (x86_64 binary) to do the real work.Our patch will fix this issue.
The last one we need to patch is in wsutil/privileges.c at line 324.Here the wsutil library called endgrent() in privilege management.However, as of Android NDK r10e API level 19, there is no declaration of endgrent() in <sys/types.h> and grp.h.Thus we have to comment out this function call to fix it.It seems safe to do so, but I have not investigate this issue throughly.Interestingly, the Android NDK r12b API level 23 have better support of privileges in <sys/types.h> and grp.h and implemented this function.Unfortunately, however, as my previous post has pointed out, the attempt of cross-compiling GLib is not successful using Android NDK r12b.One possible way to keep endgrent() is that you get the GLib cross-compiled using NDK r10e, and then cross-compile wireshark using NDK r12b.This way, this patch can be probably skipped, but any complication raise from the inconsistent NDK versions is unknown.
Finally, if you are using NDK r10e, you can apply the following patch file without patch the source codes manually.
Save it as wireshark-android.patch, and do
With all the prerequisite ready, we can begin cross-compiling wireshark.
Unable To Use Androiddump In Windows With . - Wireshark
First we need to set the environment variables to use Android cross-compilers, as the below script shows.The majority of the script is the same as the script we used for cross-compiling GLib.The only difference is the compiler flags part.
Then, run autogen.sh, if it succeeds you should expect to see the similar output.Fix any error according to its output.
Next, configure the parameters using the following.
38 Best FireStick Apps (Sep 2019) Free Movies, Shows, Live TV, Sports
We just want the basic Wireshark libraries (libwireshark.so, libwsutil.so and libws) working for Android, so I disabled most of its plugins, including pcap.You may want to keep pcap by using with-pcap to capture packets if you do not have packet capture program for Android.You can tailor the configure parameters to your own need, but probably you need to handle more dependencies.For example, if you want to use pcap, you need to cross-compile libpcap as well and add -lpcap in the LDFLAGS.That will not be too hard because there’s lots of tutorials and ready scripts to cross-compile libpcap for Android.
Finally, cross-compile Wireshark and install it to ${PREFIX}:
Want To Test My Android For Hacked Activity [closed] - Ask .
To make the process easier, you can also run the script that I made.
When I write this post, it has been seven months since my first successful attempt in cross-compiling the Wireshark libraries for Android.Back then I cross-compiled the Wireshark libraries for Android using Wireshark 2.0.1 version on Ubuntu 14.04.But honestly, I spent nearly three days compiling, haunted by various strange errors here and there.So I know how it would be useful to help save someone efforts worthing at least 10+ hours.I should have posted the detailed steps then, but I was so busy to do so.If I do not write it down now, many of the obstacles that I met and solutions I found online would have be forgotten.To ensure the documented steps are still working, I took the newest stable version of Wireshark which is 2.0.4, and re-built it on a clean installed Ubuntu 16.04 virtual machine.Now, I finally have found some time to document the detailed steps in this post.Hope it will be useful.Sincerely thanks to many of the helpful discussion threads in Wirshark-dev mailing lists, as well as other blog post on cross-compiling for Android.
- [1] https://en.wikipedia.org/wiki/Wireshark
- [2] https://www.wireshark.org
- [3] https://play.google.com/store/apps/details?id=lv.n3o.shark&hl=en
- [4] https://gist.github.com/nddrylliog/4688209
- [5] http://linux.die.net/man/3/endgrent
- [6] http://lists.mindrot.org/pipermail/openssh-bugs/2013-April/012015.html
- [7] https://bugzilla.mindrot.org/attachment.cgi?id=2233&action=edit
- [8] https://www.google.com/search?q=cross+compile+wireshark